It is important to assess whether you are currently utilizing an outdated version of the Chrome browser, as this could inadvertently expose you to browser hijacks, thereby compromising your online security and leading to a range of frustrating issues.
This article examines the nature of browser hijacks associated with outdated Chrome versions, outlines the signs that may indicate your browser is vulnerable, and discusses the risks associated with neglecting updates.
Additionally, it offers practical guidance on how to check for updates and enhance your browsing security. Staying informed is crucial to maintaining a safe browsing experience.
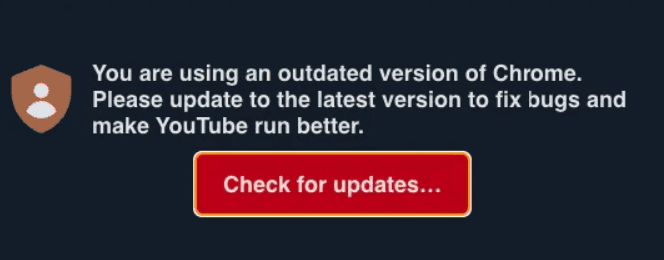
Understanding the “You Are Using An Outdated Version Of Chrome” Browser Hijack
The “You Are Using An Outdated Version Of Chrome” message is a common browser hijack that tricks users into downloading malware. This deceptive tactic, often associated with the SocGholish campaign, redirects users from legitimate websites to malicious ones displaying fake update warnings.
How the Hijack Works
Cybercriminals compromise vulnerable websites by injecting them with scripts that trigger the redirect. Unsuspecting users attempting to access these legitimate sites are instead sent to pages displaying the false warning. The message claims the user’s Chrome browser is outdated and prompts them to download a supposed update. However, clicking the download link leads to malicious files disguised as updates, often with names like “Auto.Update.Zip” or “Chrome.Update.zip.”
What Happens After Downloading the Fake Update?
These malicious files typically contain malware such as:
- NetSupport Manager RAT (Remote Administration Tool): This allows attackers to remotely control the infected computer, potentially stealing data, installing more malware, or spying on the user.
- Other Malware: The fake update can also install various other forms of malware, including ransomware (which encrypts files and demands a ransom for their release), adware (which floods the user with unwanted advertisements), and spyware (which secretly monitors the user’s activity).
How to Protect Yourself
- Be Skeptical of Pop-ups: Exercise caution with any pop-up message claiming your browser is outdated, especially if it appears on a website you don’t fully trust.
- Update Chrome Directly: Always update your Chrome browser through the official settings menu (Menu > Help > About Google Chrome). This ensures you’re getting a legitimate update from Google.
- Use a Reliable Antivirus: Install and regularly update a reputable antivirus program to detect and block malware.
- Enable Safe Browsing: Ensure Chrome’s Safe Browsing feature is turned on (Settings > Privacy and security > Safe Browsing) to protect against dangerous websites.
- Keep Software Updated: Regularly update your operating system, browser, and other software to patch security vulnerabilities that attackers could exploit.
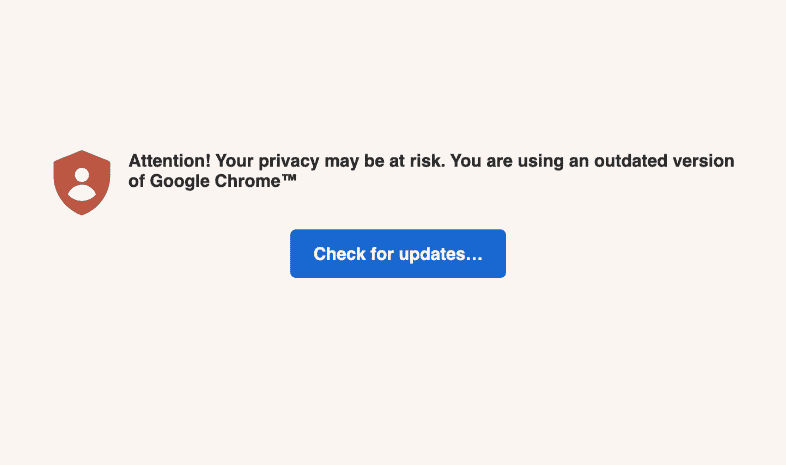
Removing the Hijack
If you suspect your browser has been hijacked, follow these steps:
- Close the Fake Warning: Immediately close the pop-up message without clicking any links.
- Scan for Malware: Run a full scan with your antivirus software to detect and remove any potential infections.
- Clear Browsing Data: Clear your browser’s cache and cookies (Settings > Privacy and security > Clear browsing data).
- Reset Chrome Settings: If the problem persists, reset Chrome to its default settings (Settings > Reset and clean up > Restore settings to their original defaults).
Staying Safe Online
The “You Are Using An Outdated Version Of Chrome” hijack is a reminder of the importance of online safety. By being cautious about pop-ups, updating software regularly, and using antivirus protection, you can significantly reduce your risk of falling victim to such scams.
Additional Information: Understanding Browser Hijackers
Browser hijackers are a type of malware that modifies browser settings without the user’s consent. They can change the homepage, default search engine, and install unwanted toolbars or extensions. This can lead to unwanted redirects, excessive advertising, and potential exposure to further malware.
Common Symptoms of a Browser Hijacker:
- Unwanted Redirects: Being redirected to websites you didn’t intend to visit.
- Changes to Homepage or Search Engine: Your browser’s homepage or default search engine has been changed without your permission.
- New Toolbars or Extensions: Unfamiliar toolbars or extensions appear in your browser.
- Increased Pop-ups and Ads: You experience a sudden surge in pop-up ads and other unwanted advertisements.
- Slow Browser Performance: Your browser becomes noticeably slower or unresponsive.
How to Avoid Browser Hijackers:
- Download Software from Official Sources: Only download software from official websites or trusted app stores.
- Pay Attention During Installation: Be careful when installing new software and pay attention to any bundled offers or additional programs.
- Use a Pop-up Blocker: Enable your browser’s pop-up blocker to prevent unwanted pop-up windows.
- Be Cautious of Links: Avoid clicking on suspicious links in emails or on websites.
By understanding how browser hijackers work and taking preventive measures, you can maintain a safer and more secure online experience.
Key Takeaways:
- An outdated version of Chrome can leave your browser vulnerable to security threats, compatibility issues, and performance problems.
- Regularly checking for updates and enabling automatic updates can help prevent an outdated version of Chrome browser hijack.
- Be cautious of suspicious websites and links, and use antivirus software to protect against potential hijacking attempts.
What Is the Outdated Version of Chrome Browser Hijack?
The term “Outdated Version of Chrome Browser Hijack” refers to a malicious attack in which cyber criminals exploit older versions of the Chrome browser to gain unauthorized access to users’ systems. This type of hijacking is often associated with the SocGholish scam, which targets users through misleading pop-up warnings that assert their browser is outdated.
By taking advantage of security vulnerabilities present in these outdated browsers, cyber criminals can redirect users to harmful websites, potentially resulting in identity theft and the compromise of sensitive personal information.
How Does It Happen?
The hijacking of an outdated version of the Chrome browser occurs through various vectors, predominantly via malicious websites that host adware applications and intrusive advertisements intended to deceive users into downloading harmful software.
Cyber criminals frequently utilize tactics such as phishing and deceptive online pop-up ads that present fraudulent warning messages, encouraging users to make impulsive decisions that may result in the involuntary download of malware, thereby compromising their privacy and security.
What Are the Signs of an Outdated Version of Chrome Browser Hijack?
Identifying the signs of an outdated version of the Chrome browser being hijacked is crucial for computer users in order to safeguard themselves against potential threats. Several key indicators should be monitored. Common signs include frequent pop-up errors that disrupt the browsing experience, the emergence of unwanted features or extensions within the browser, and unexpected alterations to browser settings that may compromise user security and increase the risk of identity theft.
Many users may observe a rise in unsolicited advertisements that appear randomly, hindering access to the content they intend to view. This phenomenon, often referred to as adware, is a typical symptom of a browser hijacking. If the homepage or search engine settings change without user consent, this could indicate the presence of a stealthy browser hijacker.
Other warning signs include:
- Unfamiliar Toolbars: New toolbars may appear without any installation by the user.
- Altered Privacy Settings: Changes to security or privacy settings that result in less secure browsing.
- Performance Lag: A noticeable decrease in website loading speed, often attributable to background malware processes.
Each of these indicators should prompt immediate concern regarding potential security breaches. Therefore, it is essential for browser users to remain vigilant and proactive in protecting their online safety.
What Are the Risks of Using an Outdated Version of Chrome?
Utilizing an outdated version of the Chrome browser presents users with several risks, primarily arising from security vulnerabilities that cybercriminals may exploit to initiate malware infections.
These vulnerabilities can lead to significant compatibility issues with newer web technologies, resulting in performance problems that adversely affect the overall user experience.
Furthermore, the likelihood of privacy concerns escalates considerably, as outdated browsers may lack critical updates required to safeguard sensitive personal information from being tracked or compromised by malicious actors.
Security Vulnerabilities
Security vulnerabilities present in outdated versions of Chrome render users highly susceptible to various cyber threats, including identity theft and exploitation by malicious tools. These vulnerabilities can be exacerbated by unsafe browser plug-ins that cybercriminals employ to infiltrate systems and gain access to personal information, ultimately compromising user security.
For instance, an outdated version of the browser may lack critical updates designed to address known vulnerabilities, leaving users vulnerable to attacks such as phishing and malware installation.
Statistical evidence indicates that nearly 50% of users fall victim to phishing scams as a result of outdated software. When a malicious browser extension is installed, it can discreetly monitor user activity, capturing sensitive information such as passwords and credit card numbers.
- In 2022 alone, over 1.5 million phishing attacks were reported, underscoring the urgent need for timely browser updates.
- The role of malicious tools is further emphasized by case studies illustrating how these extensions can redirect users to counterfeit websites, thereby increasing the risk to personal security.
Therefore, it is essential for users to maintain the latest versions of their browsers to protect their personal information from these escalating threats.
Compatibility Issues
Compatibility issues frequently arise when users operate outdated versions of Chrome, as these versions may lack support for recent installations of web applications and may not render legitimate websites accurately.
This situation often results in users being unable to access essential features or services on websites that depend on modern browser capabilities. Specifically, the lack of support can lead to significant obstacles when users attempt to interact with advanced functionalities such as interactive dashboards, multimedia content, or secure payment gateways.
- Users often find that third-party graphical content does not display properly, which hampers productivity and leads to dissatisfaction.
- Additionally, outdated browsers are more susceptible to security vulnerabilities, exposing users to potential cyber threats.
Therefore, maintaining an updated version of Chrome is imperative, not only for improved functionality but also for ensuring a safer and more seamless browsing experience.
Performance Problems
Performance issues are commonly observed in users utilizing outdated versions of Chrome, which can result in a significant decline in system efficiency. Such browsers frequently become encumbered by unnecessary applications that deplete system resources, leading to slower loading times and increased lag while browsing the internet.
When users operate on outdated versions of Chrome, they may begin to experience various negative effects on their browsing experience. Typical symptoms include noticeable delays in page loading times, particularly for media-intensive websites, as well as freezing or stuttering during video playback.
- Increased memory usage
- Unresponsive tabs
- Excessive CPU consumption
These factors can also become evident, rendering routine tasks cumbersome. The presence of unwanted extensions and plugins can exacerbate these issues, further straining available system resources and resulting in an overall frustrating user experience. It is essential to ensure that browsers are kept up to date to mitigate these performance challenges.
How to Check for an Outdated Version of Chrome?
Checking for an outdated version of Chrome is crucial for ensuring browser security and optimal performance. Users have the option to either conduct a manual check or utilize Chrome’s built-in update feature for this purpose.
A manual check enables users to compare their current version of Chrome with the latest available update, while the built-in update function can automatically detect and install essential browser updates, thereby reducing the risk of downloading malware.
Manual Check
A manual check of the Chrome browser is a straightforward procedure that enables users to confirm whether they are utilizing the latest version of the software by accessing the browser settings. Users can navigate to the ‘About Chrome’ section within the settings to view the current version number and determine if any updates are available for their system.
To initiate this process, open the Chrome browser on the device. In the top right corner, click on the three vertical dots to access the menu. From there, proceed to Settings, which will direct you to a new page containing various options.
Locate the About Chrome section, typically situated at the bottom of the left navigation pane. Clicking on this section will prompt Chrome to automatically check for updates. If an update is available, it will begin downloading immediately, and upon completion, users will be given the opportunity to relaunch the browser.
- Step 1: Open Chrome and click on the three dots.
- Step 2: Navigate to Settings.
- Step 3: Locate and click on About Chrome.
- Step 4: Allow time for the update check and follow any prompts provided.
Regular updates can significantly enhance both the security and performance of the browser, making it essential for users to remain informed about their browser’s status.
Using Chrome’s Built-in Update Function
Utilizing Chrome’s built-in update function is an effective approach to ensure that users operate the most secure and up-to-date version of the browser, as it automates the update process. This function systematically checks for available updates and seamlessly downloads them, thereby minimizing the risk of users being exposed to vulnerabilities associated with outdated software. If you see a fake warning message indicating “You Are Using An Older Version Of Chrome,” it could be a part of the SocGholish scam, which aims to download malware onto your system.
This feature not only conserves time but also significantly improves the overall browsing experience by providing the latest security patches and performance enhancements. When Chrome automatically updates, it safeguards users against newly identified threats, including those from malicious extensions and unwanted programs, thereby mitigating potential risks linked to browser vulnerabilities.
To further emphasize the importance of maintaining an updated browser, consider the following key points:
- Automatic updates operate quietly in the background, requiring no manual intervention, which allows users to remain focused on their online tasks.
- This functionality aids in preventing exploits that often target unpatched software, thereby enhancing the security of personal data.
- Regular updates ensure compatibility with new web standards and features, thereby improving the overall usability of the browser.
Leveraging Chrome’s update feature is crucial for sustaining a secure and efficient online environment.
How to Update Your Chrome Browser?
Updating the Chrome browser is essential for maintaining both security and functionality, preventing issues like data tracking and protecting personal details. Users may choose to enable automatic updates for seamless maintenance or opt for manual updates when necessary.
Automatic updates enable Chrome to routinely check for and install updates without requiring user intervention. Conversely, manual updates can be executed by accessing the browser’s settings to download the latest version, thereby minimizing the risk of malware infections.
Automatic Updates
Enabling automatic updates in Chrome is a proactive strategy for users to maintain a secure and up-to-date browsing environment. This feature facilitates regular checks for updates and installs them in the background, thereby eliminating the necessity for users to manually initiate the process.
By utilizing this capability, individuals can significantly improve their online experience. With automatic updates, users benefit from the latest security patches and enhancements without any additional effort.
- Security: Regular updates help protect against vulnerabilities that could be exploited by malicious actors.
- Usability: Users gain access to new features and enhancements that can improve their browsing experience.
- Performance: Updates often include optimizations, ensuring that Chrome operates smoothly and efficiently.
Activating this function not only safeguards browser security but also enhances overall usability, making it essential for contemporary web users.
Manual Updates
Performing manual updates in Chrome is a straightforward process that allows users to check for available updates and install them as necessary. By navigating to the ‘About Chrome’ section within the settings, users can easily initiate the manual update process and ensure they are utilizing the most recent version of the browser.
Maintaining an updated browser is crucial not only for accessing the latest features but also for enhancing security and improving overall performance. Below are the steps to execute manual updates in Chrome:
- Open Chrome: Launch the browser on your device.
- Access Settings: Click on the three vertical dots located in the upper-right corner to open the menu.
- Navigate to About Chrome: Select ‘Help’ and then ‘About Google Chrome’ from the dropdown menu; this section will automatically check for updates.
- Install Updates: If an update is available, it will begin downloading immediately. Upon completion, a prompt will appear to relaunch the browser, allowing you to apply the changes.
Consistently performing these manual checks is essential for safeguarding against potential vulnerabilities while maximizing the browser’s functionality.
How to Prevent an Outdated Version of Chrome Browser Hijack?
To prevent the hijacking of an outdated version of the Chrome browser, users should implement proactive measures, which include:
- Enabling automatic updates
- Exercising caution when visiting suspicious websites
- Utilizing reputable antivirus software
By regularly updating their browser, users significantly reduce the risk of being exploited by vulnerabilities targeted by cybercriminals, while also maintaining vigilance against potential phishing attempts and malicious downloads.
Enable Automatic Updates
Enabling automatic updates in Chrome represents one of the most effective strategies for preventing browser hijacks by ensuring that users consistently have access to the latest security patches and features. This functionality significantly reduces the vulnerabilities that cybercriminals may exploit, thereby enhancing user safety while browsing the internet.
By allowing the browser to update seamlessly in the background, users can be assured that they are protected from potential threats. Automatic updates not only provide critical security enhancements but also introduce improved functionalities that contribute to a more efficient browsing experience. This proactive approach eliminates the necessity for manual intervention, which often leads to outdated software that may lack essential protections.
The benefits of enabling automatic updates include:
- Reducing the window of opportunity for cyber attacks
- Maintaining up-to-date interfaces with the latest features
- Promoting a safer online environment for all users
In today’s continuously evolving digital landscape, it is imperative to prioritize the protection of personal data. By enabling this feature, users take a significant step toward ensuring their online security and maintaining peace of mind. Be wary of rogue online pop-up ads that might lead to compromised websites.
Be Cautious of Suspicious Websites and Links
Maintaining vigilance regarding suspicious websites and links is essential for individuals aiming to prevent browser hijacks, as many attacks are initiated through phishing tactics that direct users to malicious sites. Identifying warning signs such as substandard website design, unusual URLs, and unsolicited pop-up advertisements can assist users in safeguarding their personal information from potential identity theft.
In today’s digital environment, where online threats are continuously evolving, the importance of vigilance cannot be overstated. Users are encouraged to adopt a proactive approach by employing various strategies to enhance their online safety.
- Scrutinize URLs: If a link appears questionable, hover over it without clicking to reveal its true destination.
- Look for HTTPS: Always verify that the website utilizes a secure connection, indicated by HTTPS at the beginning of the URL.
- Check for Contact Information: Legitimate websites typically provide clear contact details, whereas dubious sites often lack such transparency.
- Utilize Antivirus Software: Keeping antivirus tools updated can protect users from potential threats originating from suspicious websites.
By mastering these techniques, individuals can significantly mitigate the risks associated with phishing and identity theft.
Use Antivirus Software
Utilizing legitimate antivirus software such as Combo Cleaner is a fundamental aspect of preventing browser hijacks, as it offers essential protection against malware infections and privacy concerns that may arise from outdated software or unsafe browsing practices.
A robust antivirus solution is capable of detecting and eliminating harmful applications before they can compromise user data. The importance of employing a reputable antivirus program cannot be overstated; it acts as a frontline defense against a wide range of cyber threats that seek to exploit system vulnerabilities.
Key advantages of using a reputable antivirus program include:
- Continuous updates to its database, allowing it to adapt to emerging malware trends.
- Advanced features that often include browsing protection, which actively scans potentially harmful websites before users engage with them.
- Privacy-focused tools that safeguard sensitive information, ensuring data integrity.
By remaining vigilant and utilizing these methods, users can maintain their online security, understanding that proactive measures significantly enhance protection against the ever-evolving landscape of cyber threats, including threats like the SocGholish scam and forced downloads of unwanted applications.
Keep Your Computer’s Operating System Up to Date
Maintaining an up-to-date operating system is essential for optimal system performance and security, as updates frequently contain critical patches that safeguard against vulnerabilities. Users operating outdated versions of Windows 10, Windows 11, or macOS expose themselves to potential threats, including browser hijacks, ransomware, and malware infections.
These updates not only enhance the functionality of applications but also play a pivotal role in bolstering the overall security of devices. Regularly applying updates ensures that known issues are addressed in a timely manner, thereby minimizing the opportunity for cybercriminals to exploit vulnerabilities.
Whether through improving system stability or strengthening defenses against phishing attacks, the advantages of staying updated are extensive. Additionally, using tools like Combo Cleaner can help mitigate risks associated with browsing habits.
Keeping current with the latest versions can result in:
- Enhanced speed and performance
- New features and improvements to the user interface
- Compatibility with the latest software and applications including Google, Firefox, Safari, and Microsoft Edge
- Reduced risk of data loss, breaches, and exposure of sensitive private information
Ultimately, investing time in maintaining an updated operating system leads to a safer and more efficient computing experience. https://www.youtube.com/embed/D5oYrpVa1YM
Frequently Asked Questions
1. What does it mean if I receive a message saying “You are using an outdated version of Chrome browser hijack?”
If you receive this message, it means that your Chrome browser has been hijacked by malicious software or an outdated extension, potentially leading to privacy issues and exposure of sensitive private information.
2. How did my Chrome browser get hijacked?
There are several ways your Chrome browser can get hijacked, including downloading infected files or clicking on malicious links from suspicious sites instead of legitimate download links.
3. Can I still use my Chrome browser if it has been hijacked?
It is not recommended to use your Chrome browser if it has been hijacked, as it can compromise your online security and privacy, exposing your browsing habits to cybercriminals.
4. How can I remove the hijacker from my Chrome browser?
You can try removing any suspicious extensions or resetting your browser settings using the Task Manager. It is also recommended to run a full antivirus scan on your device, possibly using tools like VirusTotal.
5. What are the risks of using an outdated version of Chrome browser?
An outdated version of Chrome browser can leave your device and personal information vulnerable to cyber attacks, malware, and even ransomware.
6. How can I prevent my Chrome browser from being hijacked in the future?
To prevent browser hijacking, make sure to only download files and click on links from trusted sources. Avoid third-party graphical content and monitor for unwanted applications. Also, regularly update your browser and keep your antivirus software up-to-date.